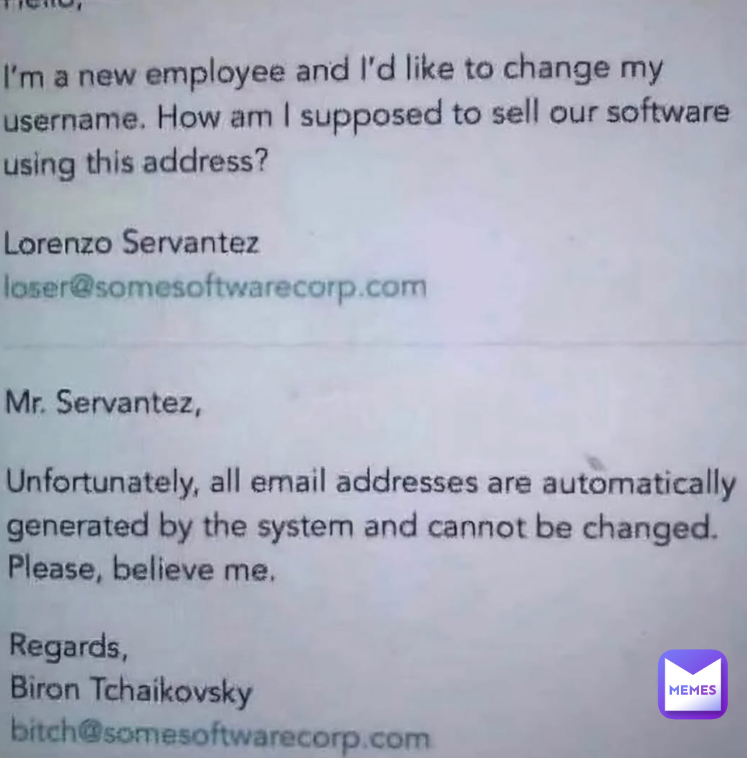
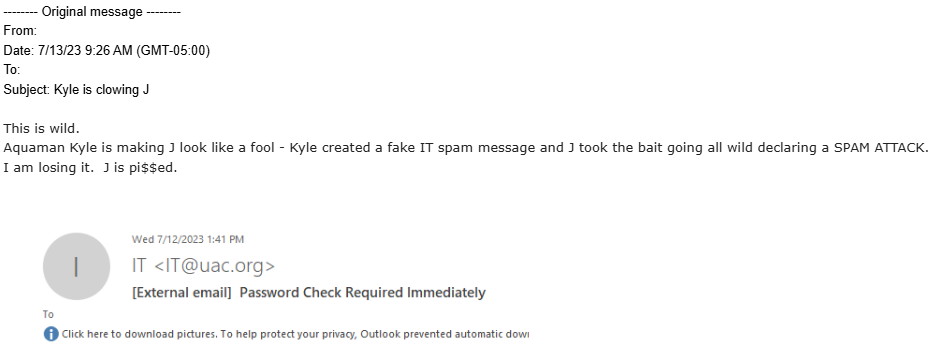
“In their world, IT Security is first then staff have email and they believe UAC should be the same way.” – Jacques Latoison
The Hierarchy Email to UAC C-Suite Management
Imagine the Urban Affairs Coalition management reading this memo and not reporting the security breach.
There was a Zoom meeting with Amerihealth on Wednesday, May 4, 2022, at 3:00 PM.
Amber Meija, Patricia Yarabinetz, and Richard Amankwah were in the meeting.
Of course, Latoison had to make a misogynistic slur about the woman asking questions.

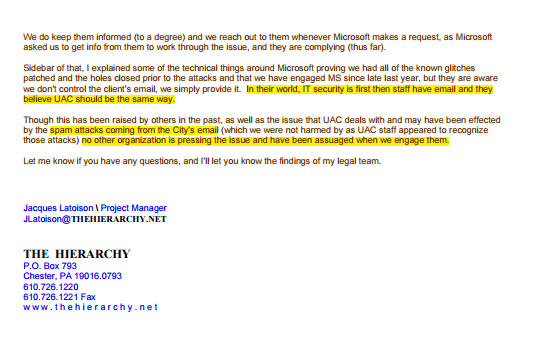
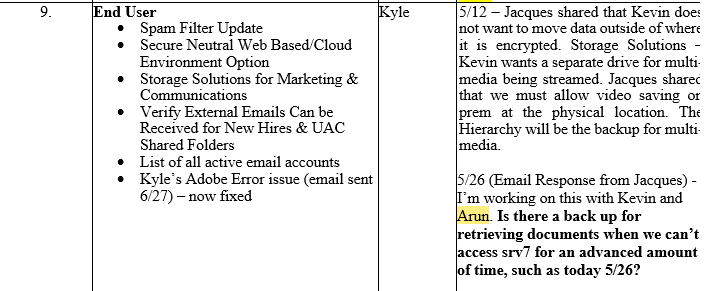
What other financial institutions’ data was compromised on 5/4/2022? Arun and Kevin were okay with not reporting this data breach?
The Hierarchy Email server was hacked
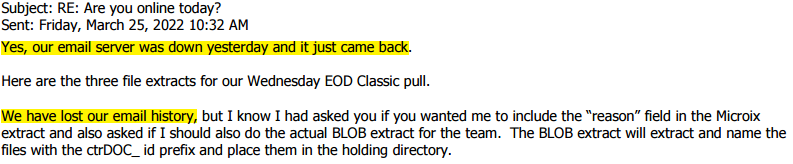
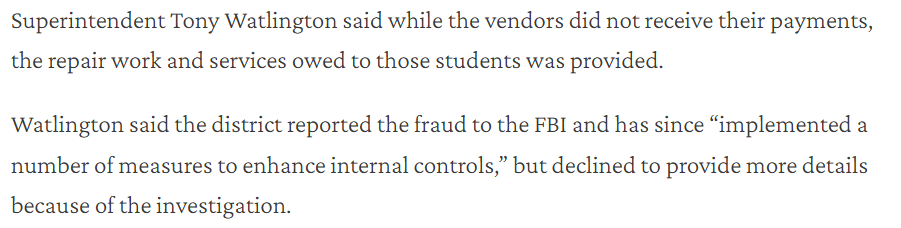
In hindsight, this makes no sense. Latoison claimed Vladimir Putin destroyed Server 4 (and its backup) and all email history. But in 2023, he sent me my PST email file that he claimed was forever lost. Kevin was throwing a fit; the downed server was delaying the NetSuite migration. Did he not recognize that The Hierarchy’s email servers had no disaster recovery plan and take action?
Jacques Latoison always blames the rUsSiAns – Putin has him on speed dial.
Vladimir is caught in the wild rocking out at 0:14!!!
Ask Vladimir why he is always picking on Latoison.
Maybe Putin stole my paychecks.
Maybe Vladimir is billing for hours nobody works.
🎶 Watch- Paul McCartney: Back in the USSR 🎶 Click Here
Why did Arun and Satterthwaite cooperate with Jacques Latoison in not reporting this to the FBI? Philly hunger relief group Philabundance had just lost nearly $1 million in a cyberattack.
UAC management claims zero responsibility for Jacques Latoison stealing money.
As far as anybody knows, neither #TurtleNeckTurner, Arun, nor Kevin has reported the heist to anybody! A way to demonstrate to the taxpayers that they do not care.
Who wants a thief in charge of their servers and emails?
Who, then, is responsible for The Hierarchy?
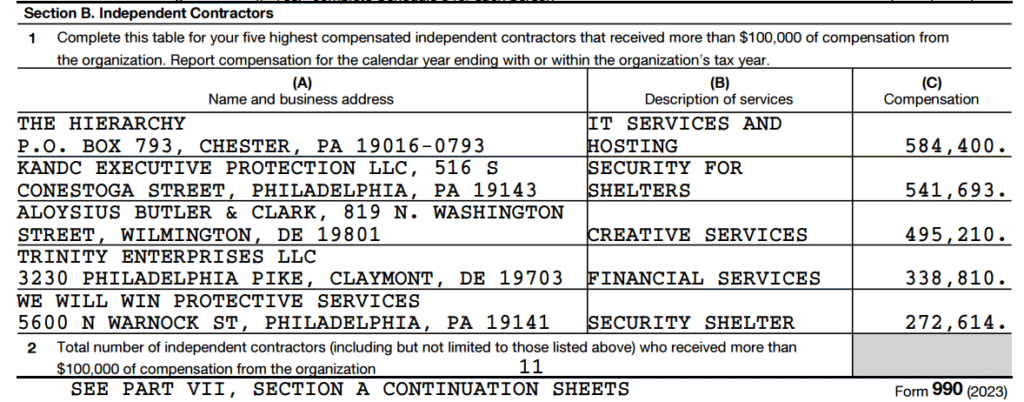
Why does UAC pay a tax cheat and embezzler with tax dollars?
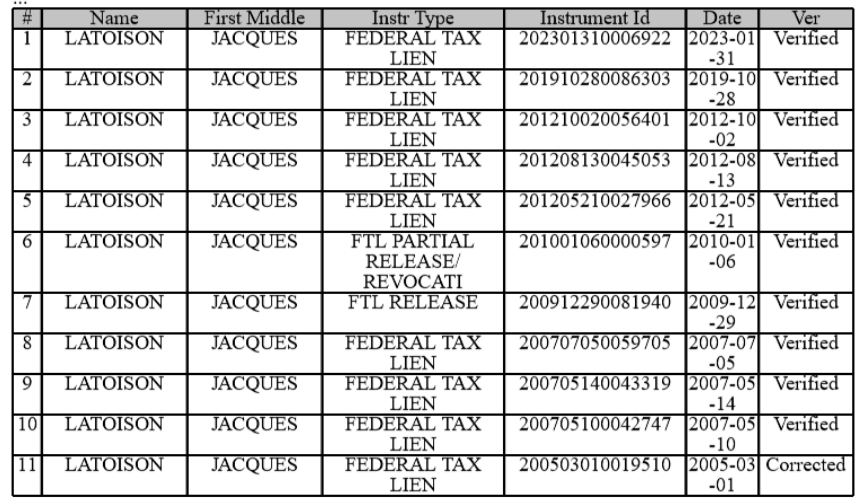
Who the hell are Jacques’ lawyers? He hired LegalZoom to send cease and desist orders to cover up the embezzled paychecks and for his billing the General Fund for time worked for ten (10) years for Mr. and Mrs. Casper the Ghost.
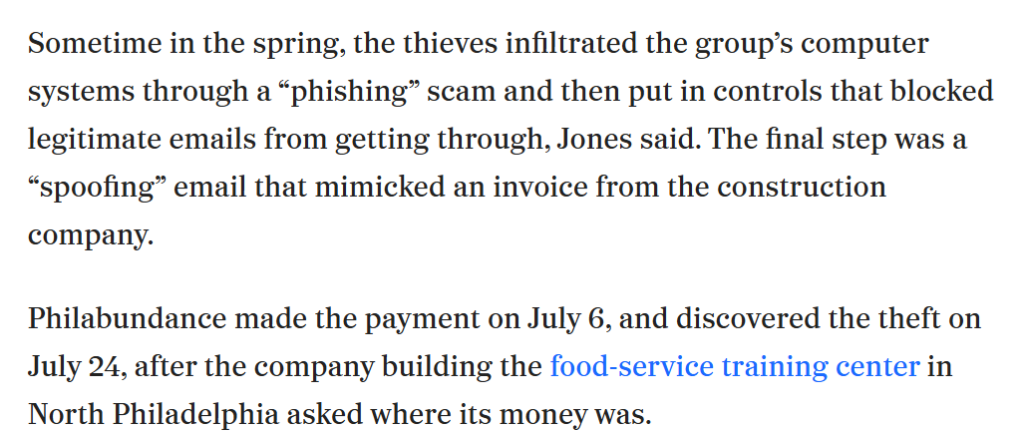
What is going on in Philadelphia?
At least this incident was reported to the FBI.
It looks like UAC has done nothing to Latoison.
Where is the insurance to pay the ripped-off vendors?
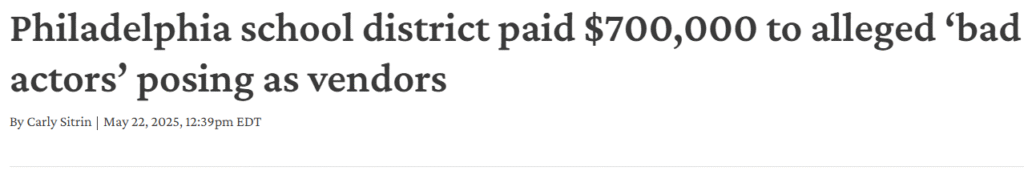
See story, click here

PST files expose government agencies to security and compliance risks, with sensitive data liable to roam local workstations, removable media, and network shares with broad permissions. Has UAC self-reported to the grants that they are out of compliance?
The Caucasian IT vendor that Jacques dislikes for being white informed me that the FBI was called in regarding a “potential” breach involving ARC in January 2022. However, UAC did not notify the FBI when its DEI IT vendor experienced issues. Jethro Bodine can’t even spell “breach,” let alone report one.

This is how Jacques treats the users UAC pays him to support. I was on call 24×7 to accommodate his after-bar hours, and UAC users can kick rocks.
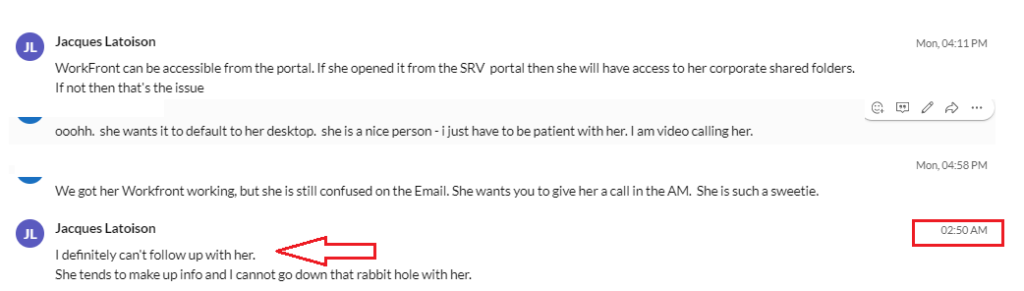
Good luck engaging with slippery Jacques. Latoison pulls a wifey five minutes into every meeting, then pulls a Houdini 👻for weeks. Every family member gets in a rear-end ⛐ collision when a deliverable is due, trees 🌳 topple on various family members’ homes like it is the 🌪️Wizard of Oz. His grown-ass kids with 5 kids of their own get a tummy 🤢 ache and a case of the squirts 💩 requiring Dr. Fauci’s team of specialists to be summoned to the 🚑 ER. Sometimes we thought he claimed Jesus recalled the same person to the pearly gates twice. 🙏🙏 Truth! We had a spreadsheet of all the excuses and the number of claims Jake at State Farm, ObamaCare, and the Undertaker must have been processing.
Latoison is such a POS that he even took 10 days pretending he had the ‘Rona during Covid 1.0.

The Latoisons were seen getting their drunk on, so I guess it was gas.
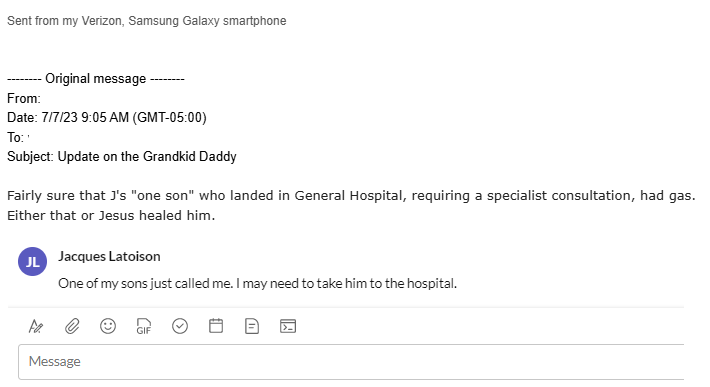

LMAO – You think I am making this shit up? Latoison claimed a tornado hit one of his mother’s houses twice. But there was no tornado in that area. Or maybe both of his mothers. He was in one meeting and pulled a wifey claiming his son got rear-ended, and told me an hour later, one of the mothers was rear-ended.
While his cousin was also recalled by Jesus, conveniently, while he was in a meeting. God works in mysterious ways. He claimed that Lisa’s father passed, but the man was white; Lisa was not listed as a relative.
Was the 3/22/2022 “The Hierarchy” Server 4 email meltdown a harbinger of the May 2022 data breach? Was this May 2022 data breach the harbinger of the May 2023 data breach? Did Crum & Forster cover the March 2022 Putin attack? Server 4 was never replaced. Was the 3/22/2022 Russian Server 4 email attack reported to the FBI?
The U.S. Department of Justice’s (DOJ) increasingly active Civil Cyber Fraud Initiative has made compliance with cybersecurity requirements a False Claims Act (FCA) enforcement priority—meaning that grant administrators and compliance staff must understand the need to keep organizational systems secure or risk significant legal exposure.
Click Here
Arun works directly with Jacques Latoison, and Latoison speaks on behalf of Kevin Satterthwaite. It looks like the tax cheat embezzler Slippery Latoison is in charge of UAC.
I never knew who the legal team was that advised The Hierarchy to not report data “BREECHES” until Crum & Forster revealed themselves. Maybe HHS needs to ask Crum & Forster what they determined. We learned Microsoft allegedly wasn’t involved nor assisting; The Hierarchy allegedly does not appear to be a Microsoft Certified Partner. The Blockbuster-era MCSE certifications allegedly seem to have been bogus.
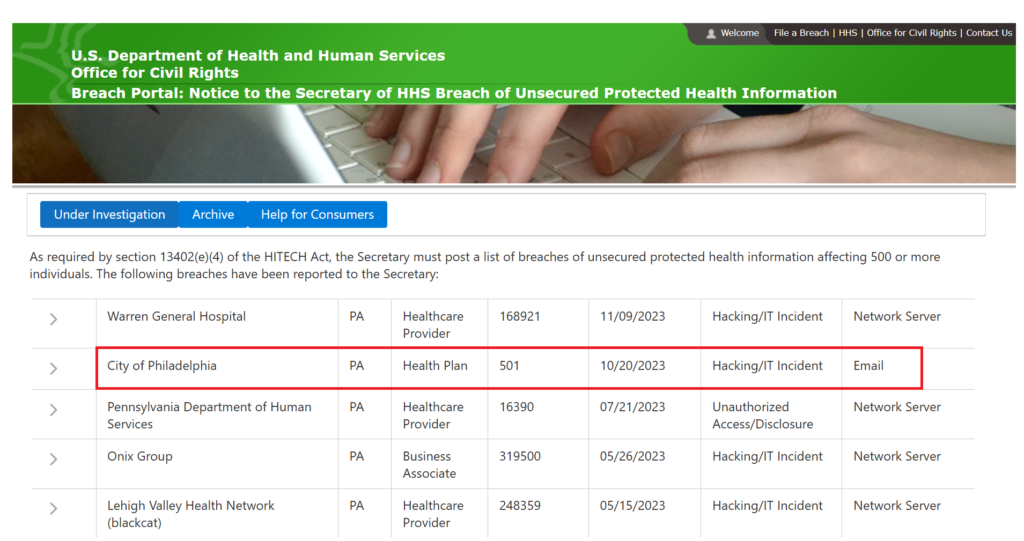
The 2023 case is still listed as “under investigation”. The person who reported it still has not been paid, and it appears UAC is retaliating further against the individual who made the report.
The legal goons are demanding that the evidence be destroyed, and now Cohen Seglias has identified itself as his legal team.
Link: Data Breaches Under Investigation
HATING ON THE CAUCASIANS
Somehow, Jacques Latoison kept forgetting I am a hated Caucasian. When an EDP user phoned to say that CareWare was popping up on their portal, I alerted the user to let Carlos know. EDP was supposed to be on their own server, that they pay for. After this rage against the Caucasians, I received another rant about #CaucasianRic and some Caucasians he hated at PHMC (Public Health Management Corporation). Latoison publicly ranted that UAC was unfair to him, claiming they paid Caucasians first.
UAC signs a Medicaid Certification Program Income form. The Hierarchy is responsible for CareWare. I believe Medicaid would be interested to know that The Hierarchy has embezzled the workers’ paychecks and fired an employee, partly for refusing to continue working for free to support CareWare on a server that she believed was not HIPAA compliant. Jacques Latoison claimed there was no money to pay the worker for supporting CareWare, but we know Latoison 🤥🤥 lies like a rug.
Has Anybody Seen the Executives’ Emails and Files?
Where are the Server 4 emails and backup, which Latoison claimed Putin destroyed?
There is no record of its demise being reported to the FBI.

Would you trust your company’s EMails to Jacques Latoison, who:
– Claimed the Russians destroyed his entire EMail server and its backup.
– Refuses to report emails being hacked.
– Sends passwords directly to Hotmail, Gmail, AOL, and Yahoo emails without encryption.
– Laptops in the offices can have guest log-ins so everybody can share.
– Sends passwords via email to Black Cipher Security cybersecurity 🤡🤣
– New user account passwords never need to be changed.
– Expiring web passwords offer the option to “Use the button below to continue with the current password.”
– Uses weak passwords and shares admin passwords.
– Admin passwords are stored in Word documents.
– HR laptops do not go to sleep or turn off or lock when the laptop screen is closed.
– No confidentiality agreement on contractors or family members being paid
under the table.
— Still running MS Office 2016 on RDP because older apps have not been upgraded.
– Ineffective offboarding of fired employees leaves the email open until the user signs out or the email server is booted. Fired workers have had access to their email for 8 hours.
– Contractors are required to use their personal computers.
– He embezzled paychecks and demanded confidential information be copied to jump drives and mailed to his company’s PO Box, which was returned as undeliverable.
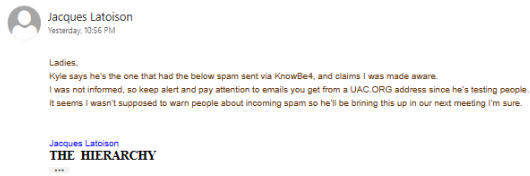
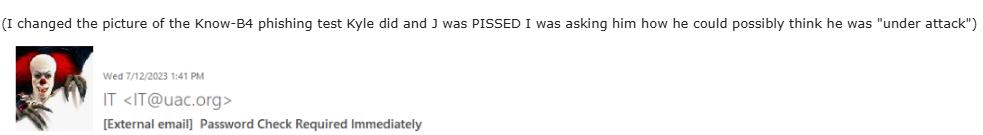
😬🤡🤣🤣 Failed to recognize his own client’s phishing test, declaring Vladimir Putin had attacked his email server again 😬🤡🤣🤣
Stephen King did it.
One of the funniest pathetic moments at UAC was when Sharmain downloaded an attachment clearly from a spammer that infected the entire joint with malware. She needs to stick to a fountain pen and paper.

SF Jazz Sues Shitty IT Provider for Negligence
SFJazz sues tech provider over ransomware attack that crippled operations.
Click here
“Despite specific contractual obligations to monitor backups and maintain system health, Aldrich allegedly failed to implement necessary software updates and neglected to secure the backup passwords needed for recovery.”
The Hierarchy got a raise.
UAC chose instead to sue the person who reported the data breach and embezzlement.
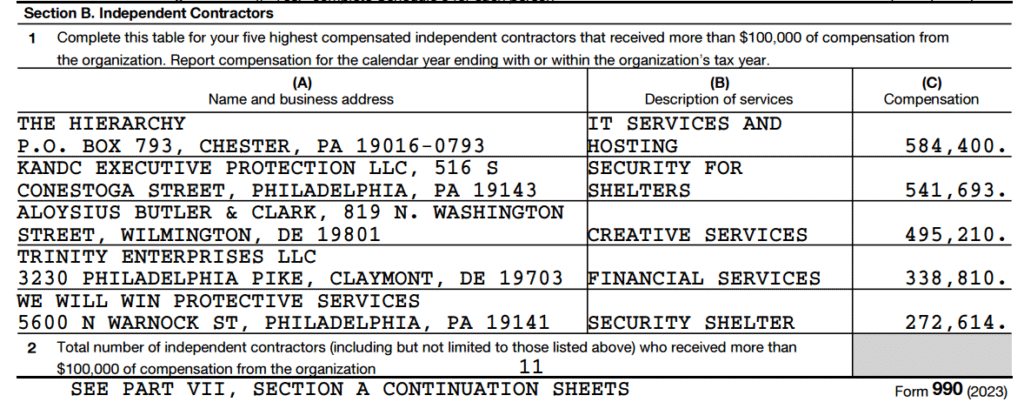
Failure to report a Data Breach
“Government contractors and other recipients of government funding are accountable for violating cybersecurity requirements and placing government data and security systems at risk. Federal rules and obligations attach to federal funds, even where those funds are first passed through state governments.” **
- knowingly providing deficient cybersecurity products or services;
- knowingly misrepresent cybersecurity practices or protocols; or
- knowingly violate obligations to monitor and report cybersecurity incidents and breaches.
In May 2022, the programmer notified UAC management that there were concerns that the CAREWare jProg (AIDS) database might reside on a non-HIPAA-compliant server. Passwords are being shared. Unauthorized users on the server portal saw the shortcut to the CAREWare application, causing alarm and confusion. Unannounced maintenance to CAREWare was being done during business hours, crashing SRV7 and corrupting data.
The Department of Human Services (DHS) is responsible for the administration, oversight, development, management, regulation, enforcement, and training of licensing programs for all human service programs for providers and partners across the Commonwealth. We do not believe UAC has a DHS License.
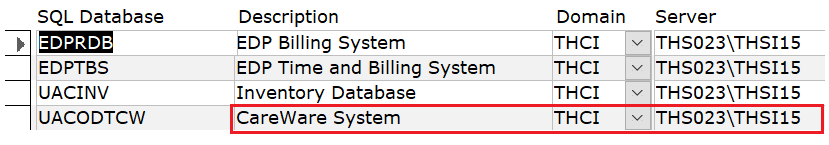
Urban Affairs Coalition refused to provide the programmer with an industry-standard Business Associate Agreement to memorialize obligations concerning Protected Health Information under the requirements of HIPAA and relevant implementing regulations, including the Privacy Rule, the Security Rule, and the Breach Notification Rule. Does UAC have a business associate agreement with The Hierarchy, ODAAT, and SELF employees who handle PHI data?
Reference: Cyber Security Article
Per the latest demands of Cohen Seglias’ cease-and-desist demands, the reporters and the law firm that the whistleblower contacted have been notified to turn over the information provided to them. HHS has also been notified to turn over the HIPAA PHI report submitted on 8/22/2023 by the whistleblower. The DOL has been notified.
I need to prepare an invoice to Crum & Forster for their SOW – now over 40 hours and no end in sight. Thank you for your business. Due upon receipt, just like your invoices.
Philadelphia Alerts Public to Recent Data Breach
You can look up HIPAA violations affecting more than 500 people on the HIPAA Wall of Shame website. Smaller violations like the HIV Testing breach out of AACO are not listed.
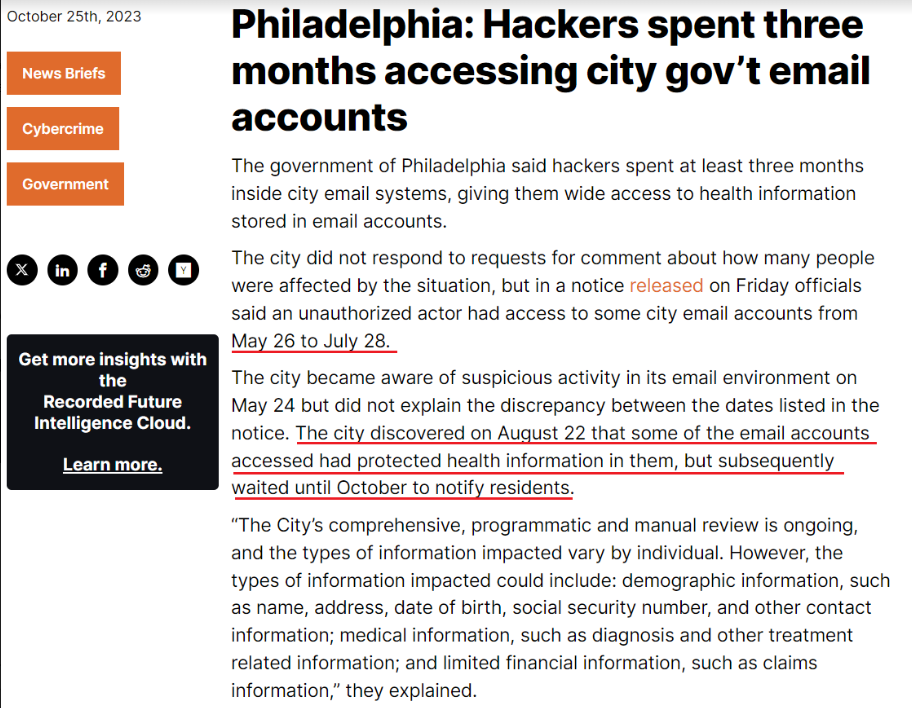
The City of Philadelphia issued a notice on October 20, 2023, reporting a security breach from May 26 to July 28, 2023. In June 2023, the programmer expressed concerns to UAC C-suite managers about a potential breach involving PHI (Protected Health Information) data in the back end of CAREWare. It wasn’t until the programmer contacted HHS on 8/22/2023 to report that CareWare patient data might be involved that action was taken. JProg has been notified. The AmerisourceBergen IT team has also been notified.
The CAREWare database is used by One Day at a Time (ODAAT). AIDS patients get a pass to the ODAAT Food Bank. Something seems amiss with The Hierarchy charging $1,950 monthly to store the CAREWare backend on its SQL Server and fees of $100 per hour to apply upgrades. Latoison said that #CaucasianRic IT vendor, Provident Technology, was unjustly awarded the CAREWare business. Provident is also charging $3,748 monthly for ODAAT hosting. Latoison said his friend Mel Wells, ODAAT President and UAC Board Member, wants The Hierarchy to have the entire ODAAT contract. The only issue is a woman named Jennifer who “forced her way in”, requesting lower hosting fees, standing in their way.
🚩🚩I was told not to enter my hours supporting CAREWare.
UAC supported Jacques Latoison in forcing a person to work for free.🚩🚩
New email users of UAC receive their login IDs and passwords via email to their Gmail, Yahoo, Hotmail, and other less secure email accounts. These passwords do not comply with industry standards, and frequently, the emails end up in the spam folder. Why are login credentials being sent to personal email accounts that might be shared with family members? Additionally, why is the programmer’s industry-standard random password generator application not being utilized as presented to the UAC auditors? The Hierarchy password protocol and procedures are the same ones used in 2010. 🦖
URBAN AFFAIRS COALITION
NEW EMPLOYEE EMAIL SETUP
Arun Prabhakaran pays this ass-clown $500,000 annually. Crum & Forster is insuring this uncredentialed vendor. Who at Crum & Forster signed this insurance policy? Some boomer executive who writes their passwords on sticky notes on display during Zoom meetings? Who the hell is using Netscape? That was shit-canned in 2008.
Good luck explaining this level of carelessness, Crum & Forster, when the next “brEEch” happens.

Did Latoison tell the UAC insurer that he was issuing passwords in the correct format? He told me he had a deadline to prove to Kyle Branch that UAC was in compliance. I created this database; I don’t think he ever used it. He just told Kyle shit to shut him up.
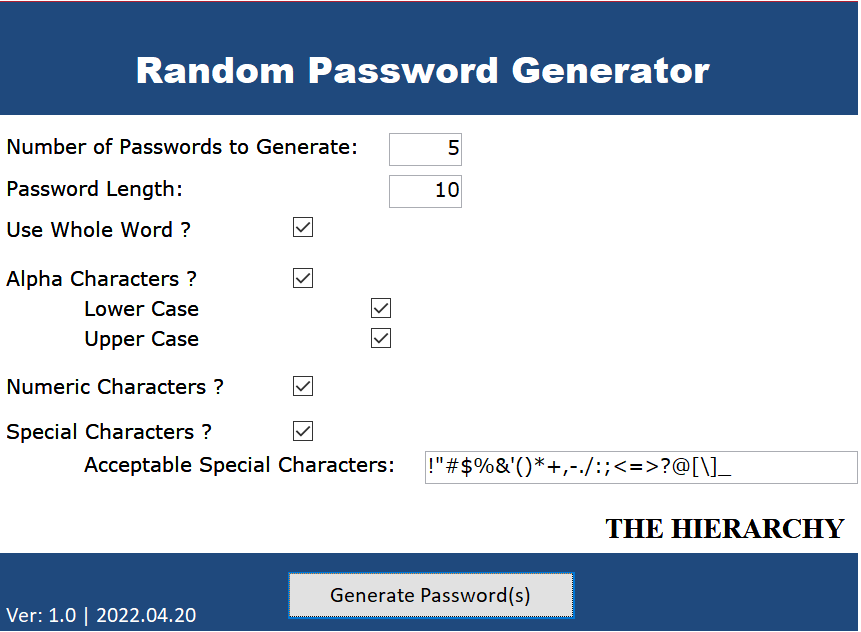
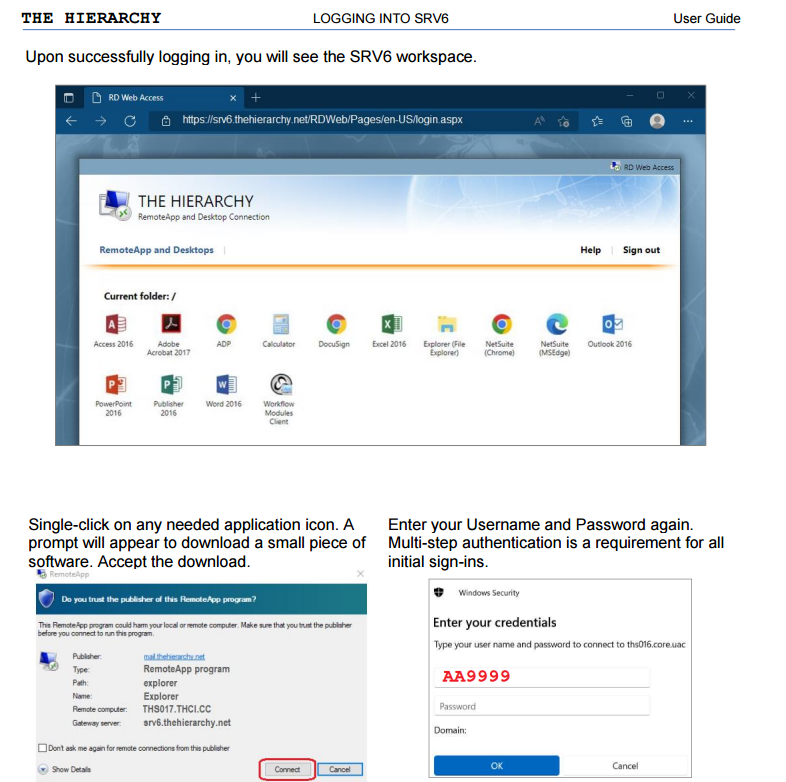
Imagine the Remote Desktop applications are the 2016 version in the year 2023.
I am fairly sure Jacques told Kyle Branch that this web-based Password Generator I created was being used instead of his 1900s passwords in April 2022 for an insurance policy requirement. Jacques was confused; he thought this was a WordPress website I created using my personal GoDaddy account that he could use for free.
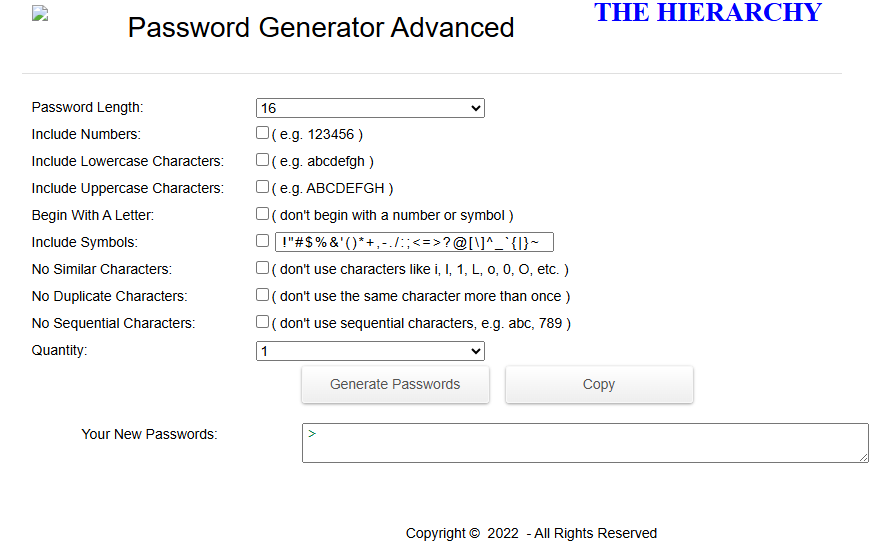
This is so Jacques-ish.